Table of Contents
The main focus of innovation has been drifting towards smartphones in the past few years. However, this focus has geared us towards other IoT Security Solutions and gadgets. Internet of Things security refers to safeguarding internet-connected devices from hackers and unauthorized access. Several Internet of Things devices are used, which start from the smart homes, health industry, and manufacturing to other various industries, whose security has emerged as the most important concern. This covers preventing data leaks, cyberattacks, and vulnerabilities in networks.
As of 2024, 35,900,145,035 data breaches have been reported to the IT Governance. Since they offer complete security services and solutions for the IoT network, the top IoT Security Solutions business is an important player in this market. They assist businesses in maintaining the security of their IoT devices by utilizing a variety of security testing techniques and instruments to identify and mitigate security threats. Custom software development companies in USA offering IoT security solutions are essential in making sure these security precautions are successfully put into place and kept up to date.
We anticipate a surge in creative and ground-breaking IoT products as it become more available to companies and their clients.
IOT security: What is it?
IoT Security Solutions secure connected devices and networks. Particularly from cyber-attacks, data breaches, and other security threats. Internet of Things devices have increased in various industries, including smart homes, healthcare, manufacturing, and transportation. Because of this, there is a necessity to secure these interlinked systems.
Evaluation Criteria
Take into account collaborations, customer support, and the caliber of hardware and software while assessing IoT custom enterprise software development companies. Seek for cutting-edge solutions that benefit customers—factors that are taken into account when ranking the best IoT custom software development outsourcing firms.
Expertise and Technical Skills
Assessment of the business’s IoT-specific proficiency, encompassing familiarity with IoT platforms, protocols, and frameworks. Taking into account their expertise in cloud integration, device management, data analytics, security, and IoT programming languages.
Experience and Track Record
An evaluation of the organization’s past accomplishments in implementing IoT security issues and solutions in various sectors and fields. An assessment of their performance in terms of client satisfaction, project complexity, and scalability. taking into account the business’s experience and solid reputation in the field of IoT development.
R&D and innovation endeavors
Analyzing the business’s dedication to innovation and continuous Internet of Things research and development. taking into account their contributions to the Internet of Things community, patents, and investments in developing technologies. Assess their capacity to offer innovative solutions and remain ahead of industry developments.
Range of Services and Solutions
Evaluation of the IoT security issues and solutions offered by the business. Taking into account their capacity to provide full spectrum IoT development services, encompassing architecture design, development, integration, strategy, consulting, and maintenance. An assessment of their ability to create unique Internet of Things apps based on customer specifications.
Customer Testimonials and Reviews
We examined customer reviews, endorsements, and case studies. Specifically, the ones that showcase the custom software development consulting successful IoT initiatives. Assess the company’s ability to meet timelines and client expectations, as well as client satisfaction and project outcomes.
10 Top IoT Security Solution Providers in USA
For dependable and knowledgeable support, it’s essential to collaborate with a respectable IoT custom software development agency USA. Find out which top IoT development businesses will have a big influence on 2025.
A3Logics
A3Logics is well-known among custom software development companies in USA that produce custom software. They have kept up with the rapid advancements in software design over time. The company has achieved certification at the esteemed CMMI Level 3. Its area of expertise is digital transformation. Known for their innovative thinking and absolute dedication to quality, they have been pacing themselves up with the fast-changing techniques in software design for years back. It specializes in digital transformation, having achieved CMMI Level 3 certification. They are known for their creative thinking and absolute dedication to the quality of service.
A3Logics has made a strong footprint in the very competitive tech industry. Consequently, creating unique Digital Transformation Services that satisfy a wide range of client needs is what the team at A3Logics loves to do. It had gained the trust of clients who view them as their chosen partners for software needs because of their diverse portfolio, which includes Fortune 500 companies and up-and-coming startups. This reputation is a result of the team’s extraordinary technical proficiency and commitment to client pleasure.
Highlights of Clientele
- A branch of IXL Learning devoted to teaching languages.
- Freight matching business headed by veterans.
- Renowned company with over 20 years of experience in providing corporate EHS software.
- Leading provider of media intelligence, including platform-wide tracking and analysis.
- Benefits administration companies for mid-market companies.
- Human resources and employee benefits are the primary emphasis of HR administration solution suppliers.
- Platforms for cloud-native human capital management.
Amazon Web Services (AWS) IoT
Offering a vast array of cloud IoT security issues and solutions, Amazon is a prominent player. To control billions of industrial, commercial, consumer, and automotive devices, the platform offers dependability and security. Analytics, management, and software are all included in AWS IoT consulting .
A few instances
- FreeRTOS is a real-time, cloud-based operating system with many ready-to-use libraries, an agile and quick kernel, and more than 40 different architecture possibilities.
- AWS IoT Core is developed to provide ease and safety when connecting devices to the cloud.
- AWS IoT Analytics is a completely managed service for the capture, processing, storage, and analysis of large amounts of data, enabled by its managed ability and even more integrations with other services, such as AWS IoT Core and Amazon S3.
Furthermore, the corporation provides an array of pre-configured and adaptable AWS IoT solutions designed for various industries, created by Amazon or its affiliates.
2. Azure IoT from Microsoft
With the help of Microsoft, another one of the well-known IoT Software Development Companies, clients can easily create scalable and secure edge-to-cloud solutions for a variety of industries, including healthcare, discrete manufacturing, the energy sector, and the automobile industry.
Services offered:
- Azure IoT Operations is the bundle of services and tools for running and managing Internet of Things installations that help a business make effective use by keeping track of the performance of equipment, identification of problems, and optimization of processes.
- Azure IoT Hub is a completely managed solution that enables two-way communication between associated devices and the cloud, allowing device administration, telemetries intake, and protected networking at scale for Internet of Things solutions.
- One of the cloud services allowing the creation of digital twins or models of real-world environments, objects, and procedures is the Azure Digital Twins. It models, analyzes, and visualizes real-world situations in very diverse industries.
- Azure IoT Edge is an IoT integration service that enables one to run cloud computing anywhere in the network. In layman’s terms, it also provides devices with the ability to process data in real time locally, which reduces latency, bandwidth consumption, and reliance on cloud connectivity.
- Azure Sphere is an end-to-end solution for securing Internet of Things devices by centralized conglomeration of hardware, software, and cloud components, incorporating elements such as secure microcontroller units, a customized Linux-based operating system, and cloud-based security services to protect connected devices from threats or vulnerabilities.
- Developers can define and execute connected solutions with the same familiar Windows tools and technologies by using Windows for IoT. Windows for IoT is a variant of the Windows operating system built for device class products that support the Internet of Things.
- Azure RTOS is a complete, real-time operating system for embedding applications. Azure RTOS also has real-time scheduling, proactive multitasking, and comprehensive middleware support, offering a dependable, portable, and efficient platform that allows for the development of linked devices and IoT Security Solutions.
Oracle IoT
You may connect your devices to the cloud using the managed Platform as a Service (PaaS) offered by Oracle’s IoT consulting services. Smart manufacturing and logistics both make extensive use of it.
Essential elements
- The ability to use JavaScript, Java, Android, iOS, C POSIX, and REST APIs to construct applications and link them to devices
- Connectivity with online services, enterprise apps, and other Oracle Cloud Services
- instruments for real-time analysis to combine and filter incoming data streams
- Data streams are automatically synchronized with Oracle Business Intelligence Cloud Service.
- Establishing trust relationships between devices and applications requires giving each device a unique digital identity.
Particle
Particle provides hardware solutions, such as development boards, gateways, and System-on-Modules, in addition to an edge-to-cloud platform for worldwide connection and device administration.
The platform places a high priority on security across all of its products, putting access control, authentication, and encryption in place to protect IoT data and devices from attacks and vulnerabilities.
Light-duty electric vehicles, HVAC systems, smart energy solutions, industrial equipment monitoring, and environmental monitoring are some of the primary application cases for Particle.
IRI Voracity
IRI Voracity is the ideal choice if you require an all-in-one data management platform that permits Big Data control throughout all phases of your business operations.
Through the use of two potent engines, IRI CoSort and Hadoop, the platform effectively manages structured, semi-structured, and unstructured data from IoT security issues and solutions, supporting a wide range of file system types on Unix, Linux, and Windows.
Essential elements
- IRI Data Manager Suite streamlines the process of getting IoT data ready for analysis and decision-making by assisting with data integration, transformation, and migration chores.
- Sensitive IoT data is protected from breaches and unwanted access with the help of the sophisticated security and privacy capabilities provided by IRI Data Protector Suite.
Apart from its strong data management features, IRI Voracity offers a wide range of support for analytics and business intelligence (BI), enabling enterprises to extract meaningful insights from IoT Security Solutions.
ThingWorx IIoT Platform
ThingWorx is an IoT Security Solutions platform that has been specially designed for and is used in a wide array of applications within the manufacturing and engineering ensembles. It provides industry-agnostic solutions to supply chain optimization, asset performance management, and remote monitoring with predictive maintenance.
It delivers one robust toolkit with which industrial process and equipment data can easily be connected, managed, analyzed, and optimized. ThingWorx is powered with the latest IoT technologies, including edge computing and machine learning, so that enterprises may get insightful information, increase productivity, and enhance decision-making throughout their entire operations.
Cisco Systems
Cisco Systems one of the leading international IoT consulting companies that sells networking and IoT solutions to companies across the world. Their IoT products thus offer connection, edge computing, security, and data management. Cisco Kinetic is a full-featured IoT platform at the network edge for secure device connectivity and data extraction.
They deliver a broad spectrum of solutions on the IoT for utilities, smart cities, industry, and transportation. Cisco has also been reliable in this sector because their good understanding of networking allows them to come up with stable and expandable IoT infrastructures that can help in seamlessly orchestrating data movement from devices to the cloud.
Cloud Salesforce IoT
Salesforce is a leader in custom software development services USA, and with the aid of IoT technologies, it expertly expands this market.
The Salesforce IoT Cloud platform collects useful data from linked devices so that you may provide individualized experiences to your clients and forge closer bonds with them. It functions in concert with Salesforce CRM: information from linked assets is sent straight to the CRM platform, where context-based actions are started right away.
When sensors identify a problem with windmill performance, for instance, the system can quickly change parameters or open a service ticket. The issue is immediately displayed on the CRM dashboard.
Essential elements
- Complete customer, product, and CRM integration
- Due to its easy-to-use point-and-click user interface, creating rules, conditions, and events doesn’t require programming knowledge.
- Compatibility with services, websites, and other goods provided by third parties
- Taking a proactive stance towards client wants and challenges
Watson IoT from IBM
A fully managed IoT integration services for device administration, adaptable and scalable connectivity options, secure communications, and data lifecycle management is an Internet of Things platform constructed on IBM Cloud. You can get insights from vehicles, buildings, machinery, assets, and objects with IBM Watson IoT.
Essential elements
- Using MQTT, data ingestion from any source
- Easy access to the most recent data in the Cloudant NoSQL database
- Dashboards for integrated monitoring to manage your assets
- Processing raw metrics with an analytics service
- The long-term data archiving solution offered by Cloud Object Storage
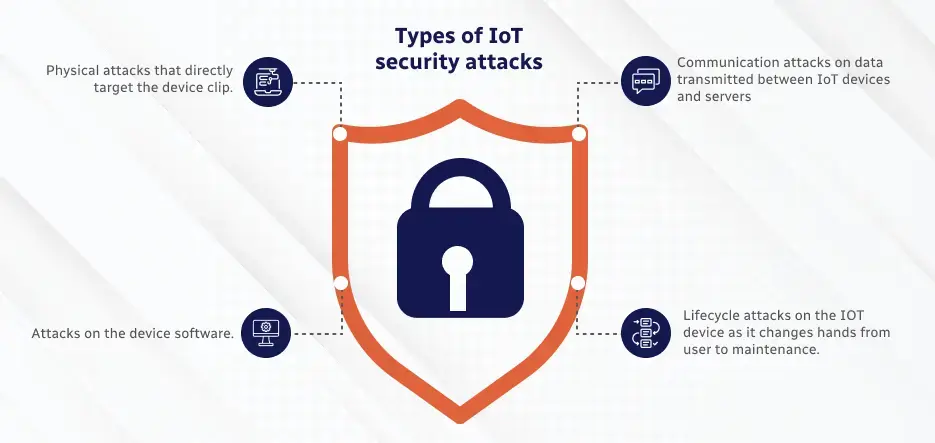
IoT Devices: Risks and Weaknesses
IoT devices are subject to a wide range of dangers and vulnerabilities, which are caused by their varied use and frequently laxer security protocols than those of traditional computing equipment. An outline of some typical dangers and weaknesses is provided below:
Weak Passwords and Default Credentials
Many of these devices come with pre-installed default usernames and passwords that are easily attacked by hackers.
Absence of Secure Update Mechanisms
Some IoT integration services do not have in place a secure update mechanism; if they do, it is not working. Therefore, in case the update mechanism gets compromised, then such devices may not be in a position to acquire updates for vulnerabilities and could easily become targets of attacks.
Insecure Data Transmission
Sensitive information may be vulnerable to interceptions or man-in-the-middle attacks. Especially on devices that do not encrypt data when transmitting or receiving.
Physical Tampering
There is a risk of physical attacks, such as device modification or data theft straight from the device, since many IoT devices may be outside or easily accessible.
Insecure Network Services
Devices that have open ports or unneeded services operating are more vulnerable to network intrusions.
Bad Software Design
A lot of IoT Security Solutions are hurriedly released onto the market with software that hasn’t undergone extensive testing, which exposes vulnerabilities.
Absence of Privacy Measures
Some Internet of Things (IoT) devices gather enormous volumes of data without the necessary privacy safeguards, which could expose user personal data.
Inadequate Network Segregation
IoT Security Solutions may not be adequately segregated when they are connected to bigger networks, which might allow attackers to access more network resources if one device is compromised.
Long Device Lifespan Without Support
Internet of Things devices may continue to operate even after they have stopped getting updates or support, which could leave them susceptible over time.
Lack of Security Standards
Because of the wide range and diversity of the Internet of Things, there are no widely recognized IoT Security Solutions or practices for devices, which causes disparities in security measures.
Embedded and Unchangeable Credentials
Some devices have firmware-based credentials that are unchangeable, leaving them permanently vulnerable in the event that those credentials are found.
Chain of Supply Vulnerabilities
Even when a device is designed to be secure, flaws may nevertheless be introduced during production or delivery.
Resource Restrictions
Most IoT devices are intrinsically resource-constrained; thus, the vast majority of them cannot support any complex security software or protocols.
These vulnerabilities reiterate that IoT security issues and solutions need to be considered during the design, design enacting, and maintenance stages of IoT devices themselves. It is imperative to solve these issues with IoT security technologies given the quick expansion and integration of IoT devices into essential infrastructure and daily life.
The Best Ways to Safeguard IoT Devices and Systems
Devices with excellent user experiences but inadequate data privacy might seriously jeopardize IoT networks and devices. It is essential to implement a set of best security practices in order to reduce these risks and improve security. To safeguard IoT devices and systems, consider the following important tactics:
Introduce the concept of IoT security in the design stage.
The best results come from implementing an IoT Security Solutions early in the design phase. By recognizing them during preparation and planning, the majority of issues and dangers that pose a risk to an Internet of Things solution can be avoided.
Security of networks
Networks are essential to a IoT Security Solutions because they provide the possibility of any Internet of Things item being remotely controlled. Firewalls, port security, antimalware programs, and blocked IP addresses that users rarely use all contribute to the stability of the network.
API safety
Hackers target sophisticated websites and businesses because they utilize APIs to connect services, transmit data, and merge different sorts of information in one location. Private data may be exposed as a consequence of an API compromise. For this reason, requests and answers using APIs should only be sent by authorized programs and devices.
Division
Businesses must segment their networks if several IoT devices connect directly to the internet. With restricted access to the main network, each device should use its own small local network (segment).
Gates for security
They provide an extra layer of protection for IoT infrastructure prior to a device’s data being sent to the Internet. They ensure that someone else cannot directly access the device by tracking and analyzing incoming and outgoing information.
Upgrades for software
We should update the software and equipment automatically or over a network connection to allow users to make changes. Adding additional functionality and helping to find and fix security flaws early on are examples of improved software.
Combining groups
The development process for IoT Security Solutions involves a large number of people. They share equal accountability for guaranteeing the security of the product during its entire lifecycle. Ideally, security experts and IoT developers should collaborate early on in the design process to exchange best practices and essential security measures.
Throughout the whole development cycle, you must maintain a defensive and proactive security policy in order to manufacture reliable products and safeguard them against cyber attacks.
he Advantages of Employing IoT Development Company
Hiring a seasoned team of enterprise custom software development companies with a focus on IoT security testing is a smart move, unless you have in-house knowledge. It’s difficult to test IoT security solutions. It covers a wide range of areas, such as hardware, firmware, mobile, web, cloud-based services, and web. These areas have the ability to impede your progress and readily take your attention away from your primary business operations. Thus, enlisting outside knowledge can be a wise strategic choice.
Here’s what you can accomplish by hiring IoT consulting companies:
Examine your architecture for IoT security.
their staff will analyze your IoT security solutions in detail and find any weaknesses in IoT devices. They’ll evaluate the strength of your application security and make sure the security and privacy features of your IoT devices are up to par. Knowing how effectively your devices and their software can survive potential security threats depends on this review.
Conduct penetration testing
Their area of expertise is penetration testing. They are able to detect vulnerabilities in your system before malevolent actors attempt to take advantage of them by mimicking actual attacks. This entails evaluating your IoT ecosystem’s hardware and software components.
Evaluate the Complete IoT Ecosystem
They take a comprehensive approach and test the entire ecosystem. This entails examining not just individual devices but also their network interactions. Their ability to offer complete security solutions stems from their ability to monitor IoT devices in their operational context.
Perform Every Kind of Security Testing
They carry out every kind of security testing, including software composition analysis and both static and dynamic analysis. By doing this, you can be sure that every part of your Internet of things system, including the software development lifecycle and device firmware, is safe from online attacks.
Evaluate the Risks
A crucial component of their service is risk assessment. They assess the possible hazards connected to your IoT security solution, giving you a comprehensive picture of your vulnerabilities and their potential effects on your company.
Assure Adherence
Lastly, they make sure that your IoT security solutions abide by the most recent rules and industry standards. Taking this precaution is essential to protect against situations in which your program is compromised. By abiding by these guidelines, They assist in preserving your clients’ trust and shielding your company from any legal or financial fallout.
Conclusion
Artificial intelligence in software development will be necessary to safeguard the next generation of IT environments due to the proliferation of IoT devices. Businesses that are actively implementing IoT devices should move cautiously and be aware of the security concerns with unreliable edge devices.
It is imperative for organizations to monitor Internet of Things traffic for unexpected risks, implement appropriate protections, assess risk, and visualize IoT assets under management. As with many other aspects of cybersecurity, action and strategy are informed by visibility, which makes the initial work of choosing an IoT security solution or putting together a plan all the more beneficial in reducing needless risk.
FAQ
1. How do start with the Internet of Things development?
Firstly, understanding the core of intrinsic technology driving the concept, such as sensors, microcontrollers, and wireless communication protocols. Once all that is in place you are ready to start your Internet of Things Development project; the next step would be choosing a development platform like Arduino, Raspberry Pi, or NodeMCU.
2. What are some benefits of the IoT?
Embedded within IoT applications are several other advantages such as better user experience, cost savings, efficiency gains, and safety and security. The adoption of IoT devices will further allow for the making of better decisions through the automation of laborious operations, maximized usage for a resource, and serving real-time operational data insights.
3. What are the core technologies behind the development of the Internet of Things?
All complete Internet of things systems share the four distinct components, such as sensors/devices, connection, data processing, and user interface. The technologies used in IoT are mainly networking and standard protocol technologies. IoT is mainly enabled by technologies and protocols, such as LTE-A, WiFi-Direct, NFC, low-energy Bluetooth, low-energy wireless, and low-energy radio protocols.
4. What is the main goal of the Internet of Things?
IoT devices are not limited to just computers and machinery. Anything can be labeled as a device of the Internet of Things if it contains a sensor and a UID. The vision and overarching goal of the Internet of Things is to have a network of self-reporting devices. These devices facilitate real-time data exchange with one other and with people.
5. How does the Internet of Things work?
IoT sensors gather data and push it to the cloud or some central hub for analysis, against which judgment calls can be made and processes automated.






