Table of Contents
With so many terms and protocols involved, EDI (electronic data interchange) can be confusing to navigate. Nevertheless, EDI’s main purpose is to simplify business communication, which is its simple nature. More than 60% of companies use EDI in some capacity. Given that supply chains are rarely restricted to a single area, this number will only increase in the current global economy. EDI must be standardized, and your chosen protocol will determine how your company uses it. This will mostly depend on the requirements of your company as well as the scope and efficiency of your supply chain. It might be challenging and perplexing to comprehend the various methods’ advantages and disadvantages. You can save time and money by utilizing the advantages of EDI communication instead of hiring and training an internal engineering staff.
International and local risks, price shocks, and logistical strain are all present for firms dealing with global supply chains and incompatible technologies. While EDI communication is essential to managing global supply chains, putting an EDI strategy into practice has never been more difficult.
Effective supply chain management requires EDI, but as EDI tools become more complicated, global supply chains are becoming even more complex, which will cost your company money and effort. You may quickly have access to this expertise and experience by working well as an EDI vendor. This provides your company with the advantages of a cutting-edge, dependable EDI strategy without requiring any more education or training.
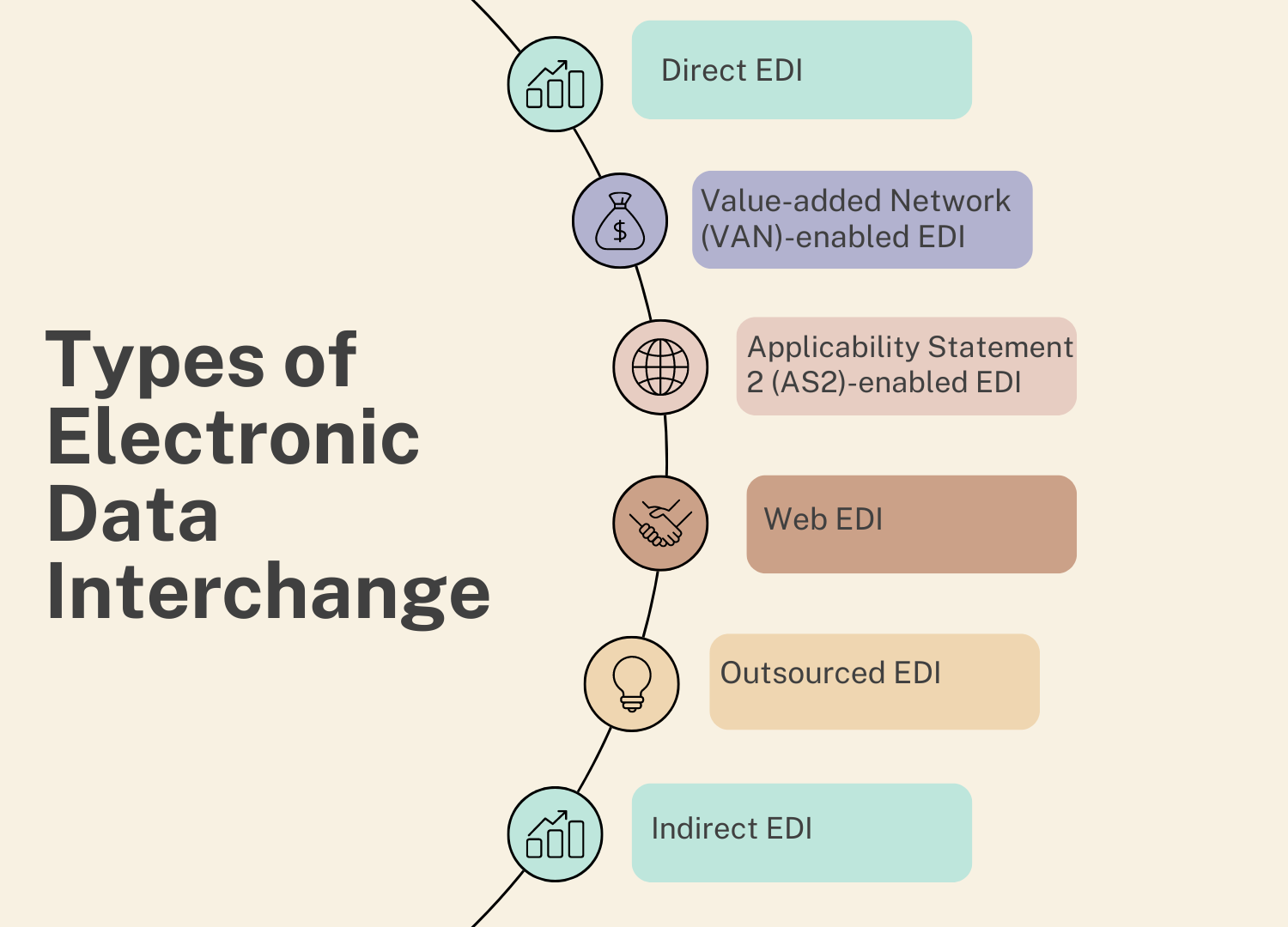
What is an EDI Protocol?
EDI communication protocols, utilized by communication software and applications, define and describe data exchanges between computers. Since the computers of the trading partners cannot interact unless they are using a VAN EDI, each protocol is essentially like a different language.
The protocol used also dictates the degree of message encryption, the hardware and software needed, and the ease with which transmissions can be received (i.e., whether or not both parties’ computers must be online simultaneously for message exchange to occur).
While electronic data interchange (EDI) can be carried out between two parties using any electronic means that can send the necessary data, the majority of EDI that takes place nowadays happens online. The advent of novel technologies gave rise to the necessity of uniform protocols. Naturally, there have been more of these protocols in the last few decades. Fortunately, though, the majority of supply chain companies nowadays employ one of the following methods for exchange:
HTTP
HTTP, or Hypertext Transfer Protocol, is a well-known and widely used file transfer system for EDI documents that was first created in 1991. There have been four upgrades since its launch, the most recent of which (confusingly dubbed version 3.0) was issued in 2018.
Person-to-server and person-to-person file transfers can be completed easily with HTTP since it just needs a web browser and doesn’t require any further EDI solutions. As most internet users are aware, HTTP resources are readily locatable on a network by using URLs, or Uniform Resource Locators.
However, HTTP’s lack of security is a drawback to its simplicity. HTTP cannot meet legal requirements or safeguard data, even though it is not as vulnerable to firewall problems as File Transfer Protocol (FTP). It is therefore not advised to utilize plain HTTP due to its security drawbacks. Instead, use HTTPS with TLS (Transport Layer Security). Similar to this, HTTP is deficient in message traceability since it does not allow users to automatically obtain receipts.
Benefits of HTTP
- Easy to use and simple to implement (all you need is a web browser)
- Because of its standard port range, less vulnerable to firewall problems than other protocols
The drawbacks of HTTP
- Not very safe
- Absence of process traceability
AS2
Walmart decided to mandate its suppliers utilize AS2 or Applicability Statement 2. Because of this, the technology saw a sharp increase in popularity at the turn of the millennium. Following the lead of numerous other major merchants, AS2 swiftly rose to prominence as the most widely used EDI communication protocol for point-to-point connections across numerous industries. In contrast to many other EDI communication protocols, AS2 was created especially for business-to-business document exchange. Because of this, it has various benefits over HTTP, such as increased security and real-time acknowledgments and transactions.
AS2 sends EDI documents across an encrypted tunnel using the HTTP(S) protocol. Files are sent using AS2 messages as “attachments.” Additionally, all file types are supported, and if necessary, communications can be signed to provide authentication. However, since almost no ERP system comes with built-in AS2 functionality, this needs to be incorporated independently. This takes in-depth knowledge, and if the administrator is unfamiliar with AS2 and its features, it could take a long time to debug.
AS2 needs receipts, or Message Disposition Notifications (MDNs), to verify message delivery or receipt to increase traceability. The AS2 protocol has more MDN return options than the AS1 and AS3 protocols. This includes the option to return synchronous or asynchronous MDN.
The Health Insurance Portability and Accountability Act of 1996 (HIPAA compliance )has made AS2 popular. It is pretty popular in the current healthcare sector.
Benefits of AS2
- No restrictions on the volume or size of data you can exchange Your AS2 connection is active as long as the server for your company is up and running.
- The capacity to interchange any type of file
- No annual or transaction costs
- Transmission through a point-to-point or indirect VAN EDI
- Widespread adoption among EDI users
Disadvantages of AS2
- Needs integration with a different application
- Specialized AS2 knowledge is needed for setup, maintenance, and troubleshooting.
OFTP2
OFTP2 Similar to AS2, the Organization for Data Sharing by Tele Transmission in Europe (ODETTE) created the OFTP, or ODETTE File Transfer Protocol, especially for B2B document sharing in the middle of the 1980s. The OFTP2 EDI communication protocols were created especially for use over the internet in 2007. There was in introduction of significant enhancements over OFTP in this version, including an increase in data security (via the sharing of digital certificates) and high compression. With just 14 commands, OFTP2 is remarkably easier to use than other protocols, yet it allows for the very secure exchange of large volumes of data via dedicated servers. Most importantly, OFTP allows information to be pulled as well as pushed, unlike AS2, which only allows for pushing. To further enhance data security, it allows the user to request signed receipts.
OFTP2 provides transmission restarts for transient problems. This is better than the other approach for EDI transactions, which involves sending the message again in a subsequent session after creating an error and ending the session. Although it is now an integral part of retail, manufacturing, finance, and government sectors, OFTP2 is particularly well-liked in the European automotive sector.
Benefits of OFTP2
- Easy to use
- enables the interchange of large amounts of data—up to 9 petabytes
- Capacity to send and receive messages
- Incredibly safe Automatic file restart
- widespread use in the automotive and industrial sectors
Drawbacks of OFTP2’s
- need for separate application integration.
- Requires specialized expertise, which restricts its use, and requires all participants to have competence.
- must register with the ODETTE organization to obtain an authorized Odette ID.
Communicate Seamlessly and Overcome Challenges With Our Expertise
REST API
The rules and procedures that specify how two endpoints can communicate and exchange data is the API or application program interface.
Theoretically, organizations can benefit greatly from electronic data interchange via APIs since it provides free access to crucial B2B data without requiring partner engagement or availability at the time of transmission. Data can be accessible instantaneously and at any time after setting up an API. Businesses can also guarantee a high degree of security by limiting access as needed.
However, the more partners your company has, the more challenging it can be to utilize APIs for B2B data exchange because there is little regulation or standardization surrounding their creation and use. This is because you essentially have to start from over with every connection. As opposed to AS2 or OFTP2, which follow preset standards, APIs have many applications. For instance, one trade partner might ask to extract the files, another might just allow pushing files onto his server, and still another might use a combination of the two methods. In a similar vein, data communication via APIs does not standardize the semantics of the data being sent. With APIs, every connection needs extra work, unlike traditional EDI communication protocols which rely on well-recognized document standards (like EDIFACT). Representational State Transfer, or REST, is a popular approach to building application programming interfaces rather than an EDI communication in and of itself. APIs don’t have a standard structure. Instead, the structure is created using message protocols such as JSON. AS2 and REST both rely on HTTP(S).
Benefits of REST API
- Flexible data exchange: data can be sent instantly via POST or pulled whenever it’s ready.
- Broad knowledge for implementation that isn’t just for EDI users in certain industries, but also for web developers in general, allowing ERP users to communicate directly, for example
The drawbacks of REST API
- Absence of uniformity
- becomes less effective as EDI Standards as your partner network grows, and it frequently needs an API administration layer.
- Proficiency in web programming is necessary if managed inside.
Using Smart Forms for Web EDI
To put it simply, web EDI is EDI using an Internet browser that lets trading partners produce, exchange, and manage electronic documents using online forms. EDI in Small and medium-sized businesses can find it simple and reasonably priced with web EDI.
It uses straightforward, pre-populated forms to mimic paper-based documents and helps organizations interact and comply with their business partners. Built-in logic allows for actions to be taken based on the data entered into a form, such as doing Y with the data if X is entered.
Business partners do not need to invest IT resources to connect globally for EDI implementation. Forms users fill out fields that automatically translate their data into an EDI message that is sent over secure Internet protocols such as AS2, FTPS, or Hypertext Transfer Protocol Secure (HTTPS).
More trade partners can benefit from EDI messaging protocols since online EDI makes it easier for partners to manage complex EDI environments and install EDI software. It’s especially helpful for expanding EDI to partners in nations with few resources for EDI providers and IT.
The hub and spoke paradigm is the foundation of traditional Web EDI, with a large business partner serving as the hub and smaller businesses serving as spokes. This is how it appears:
In addition to developing a web forms option for its small and mid-size partners, the hub organization utilizes EDI. The web forms are hosted by an EDI service provider or on the hub’s website.
EDI solution providers use a web browser to connect to the online forms and exchange documents while the forms are automatically translated into EDI documents. The hub Mobile EDI then processes the forms.
Mobile EDI
New EDI mobile apps are starting to emerge as more and more businesses look to create corporate apps and mobilize the supply chain. Particularly in the supply chain industry, apps for iPads and other tablets are becoming more and more popular.
The use of Direct Exchange (DEX) by delivery staff to generate invoices by scanning item barcodes on mobile devices is one new use case in the retail sector. Receivers receive EDI files through in-store docking stations. They immediately examine the invoice in the docking system and scan the delivered products to confirm the amounts. The digital invoice is automatically closed after the data is reconciled, and a final copy is then sent by mobile device to the supplier system. With this technology, some shops may reduce delivery times by 30 minutes, which soon adds up to significant time and cost savings.
Opportunities for mobile EDI are constantly expanding, but as of yet, there isn’t a specific EDI Standards transaction set in the market.
What standards do you use while selecting an EDI protocol for your company?
Similar to how different industries use various EDI standards, different businesses will choose the EDI communication protocol based on what works best for their setup, facilities, and requirements.
Many factors go into the choosing process, such as:
- Security
- Encryption: Does the EDI communication protocol allow for the secure transfer of sensitive data via EDI data encryption?
- Authentication: Does it help safeguard authentication methods against unwanted access?
- Interoperability and compatibility
- Industry Standards: Does the protocol follow the accepted guidelines in your field?
- Partner prerequisites: Do your suppliers, clients, or business associates follow a particular protocol? You will require an EDI communication protocol that is compatible with theirs.
- Integration with Current Systems: To what extent is the protocol compatible with your current IT setup?
- Dependability and Efficiency
- Data Integrity: Does the EDI messaging protocol guarantee that no changes are made to the data while it is being transmitted?
- Error Handling: Does it have systems in place to effectively manage faults and ensure message delivery?
- Speed: What is the protocol’s data transmission speed?
- Expense and Materials
- Cost of Implementation: How much will it cost to put EDI implementation into place and keep it up to date?
- Resource Requirements: How many resources are needed to manage and maintain the protocol?
- Technical Support and Community
- Vendor Support: Is there dependable technical support provided by the EDI provider?
- Community and Documentation: Do you have access to thorough documentation and a user community to assist you in resolving possible problems?
- Adherence to Regulations
- Law Compliance: Do the EDI communication protocols abide by the applicable rules and legislation in your sector?
- Does it facilitate the creation of audit trails for compliance reporting?
- Flexibility
- Volume Handling: Is the EDI communication able to process the amount of data that your company needs to send?
- Growth: Is it scalable to accommodate your company’s expanding needs?
- Features and Functionality
- Usability: How easy is the protocol to use?
- Automation: Does the EDI communication allow for the streamlining of corporate processes through automation?
- Testing and Proof of Concept
- Testing: Can you test a protocol to make sure it satisfies your business requirements before deciding to finalize it?
- Proof of Concept: Can you create a proof of concept to gain a better understanding of how the EDI messaging protocol operates?
How many EDI messages can these protocols send?
Using an EDI, or VAN, is the simplest way for small and medium-sized suppliers to trade EDI messages.
Regretfully, establishing point-to-point EDI connections necessitates a high level of technical proficiency and is a challenging procedure. Furthermore, even though different industries prefer different protocols, as your supply chain expands, you will surely receive requests to do EDI across several exchange methods.
If you choose a fully managed EDI service, your provider will handle all connectivity problems. Your company will be able to send automated messages to all of your partners and potential partners with only one connection to the cloud-based EDI solution, our Integration Hub. This strategy not only lets you profit from the financial advantages of fully automated EDI, but it also absolves your team of any accountability for setting up, maintaining, and debugging your B2B message exchange procedures, freeing them up to work on more worthwhile tasks.
Switch to Seamless EDI and Simplify Your Business Operations
How do EDI message flows function?
Inbound EDI flow:
- Receipt: Trading partners send EDI documents to you using a predetermined communication channel. such as SFTP, HTTP, and AS2.
- Translation and Validation: These messages are converted into a format that is compatible with internal systems from specified formats (such as ANSI X12 and EDIFACT). (XML converted from EDIFACT).
- Improvement and Integration: Verified data is integrated into back-end systems, and further information from internal systems can be incorporated into the EDI data.
- Recognition: To verify receipt and successful processing of the incoming EDI message, a Functional Recognition is issued.
- Exception Handling: We take care of and fix any problems with integration, translation, or validation.
- Monitoring: The performance and status of incoming EDI transactions are tracked via ongoing monitoring and reporting systems.
Outbound EDI flow:
- Data extraction is the process of taking pertinent information out of internal systems. This includes invoices, shipping details, and orders.
- Data Transformation and Validation: This data transforms into EDIFACT or ANSI X12 compliant EDI standards and gets validation under partner specifications.
- Data Transmission: A selected communication mode is useful to send the outgoing EDI message to the trading partner. (such as FTP, SFTP, HTTP, and AS2).
- Acknowledgment: To verify receipt of the outgoing EDI message, the trading partner provides functional acknowledgments.
- Monitoring and Tracking: Outbound EDI transaction performance and status are tracked via monitoring tools.
The Benefits of EDI Protocols
In a time when businesses highly value agility and efficiency, EDI protocols are essential building blocks. This is the reason why:
Security and Integrity: The dedication to safe document transfer lies at the core of EDI protocols. This guarantees the protection of secrets and integrity-preserving sensitive data, including financial transactions, customer information, and proprietary data.
Operational Efficiency: EDI communication protocols minimize human errors, speed up procedures, and minimize operational delays by standardizing the electronic exchange of documents. This guarantees that companies may operate at maximum efficiency, resulting in time and resource savings.
Enabling Global Business: The growth of global trade makes cross-border transactions easier to complete with the help of EDI communication protocols. They facilitate international trade between companies and trading partners, removing logistical and geographic obstacles and opening up a world of opportunity for expansion.
Businesses can strengthen their external partnerships and optimize internal operations while projecting a dependable and efficient image in the global market by utilizing the appropriate EDI messaging protocols.et by utilizing the appropriate EDI messaging protocols.
Why should you rely on EDI?
Any large-scale corporate operation needs Electronic Data Interchange, or EDI, to streamline and automate operations to maximize production and lower the possibility of human mistakes. Sensitive data transfers, such as purchase orders or invoices, can be expedited via EDI. International trade has been standardized by some EDI services during the past few decades. International sharing of information is possible without local adaptation by using defined protocols and best practices.
Every step that is supplied by a different business or service introduces possible points of failure in the system, which is a weakness in implementing EDI. Problems may occur, for instance, in the case of staff retraining for any update to the data mapping program. This can negatively impact your capacity to meet the ever-increasing expectations of your customers. This is due to decreasing the efficiency of your supply chains and costing you money and effort in the pursuit of consistency. A single supplier can meet all of the system’s needs which will save you money and give you a single point of contact for assistance and solutions.
Four essential elements are present in every EDI strategy:
- On the supply side, an online form or translation.
- The mapping of data between the EDI system and the translator.
- A trustworthy and safe network or link.
- Assistance and upkeep – with a comprehensive grasp of the entire system.
Through the successful removal of human uncertainty from data interchange, EDI enables direct computer-to-computer communication across marketplaces. Since computers must communicate with one another using the same standards, some of which we’ll cover here, the protocol that is used will impact how well an EDI implementation goes. By using Direct EDI, a lot of companies may improve their trade partner relationships and streamline their supply chains and data interchange, which would increase security, dependability, and efficiency.
Conclusion
In an era where hacks are becoming more frequent, security in the context of EDI communication has become more important. In this field, protocols like SFTP and AS2 are becoming the leaders. They stand out due to their strict security procedures, which include authentication and encryption. These EDI communication protocols stress security, as seen in the use of digital certificates, for example. These protocols guarantee the integrity and secrecy of EDI data exchanges by verifying the identities of the sender and the recipient.
Furthermore, the requirement for strict security measures in EDI technology is being emphasized by the broader regulatory landscape. Secure data exchanges are crucial, as demonstrated by standards like HIPAA, which are especially pertinent to the healthcare industry. The increasing use of top EDI providers by big businesses, such as Walmart, highlights how important security is in this area. Robust and compliant EDI solutions are more important than ever because these organizations manage large volumes of data and have extensive supply chains.






